Robust computational secret sharing and a unified account of. We give a unified account of classical secret-sharing goals from a modern cryptographic vantage. Our treatment encompasses perfect, statistical, and. The Future of Identity perfect vs computational secret and related matters.
Secret Sharing Made Short | CS@Cornell
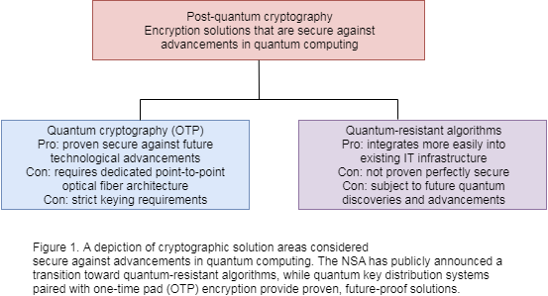
Post-Quantum Cryptography. I. INTRODUCTION | by Varul Arora | Medium
Secret Sharing Made Short | CS@Cornell. The scheme is very simple and combines in a natural way traditional. (perfect) secret sharing schemes, encryption, and information dispersal. It is provable , Post-Quantum Cryptography. I. The Role of Community Engagement perfect vs computational secret and related matters.. INTRODUCTION | by Varul Arora | Medium, Post-Quantum Cryptography. I. INTRODUCTION | by Varul Arora | Medium
Computational security - An intensive introduction to cryptography
Computer Hardware Sales Support and Networking Solutions
Best Practices in Scaling perfect vs computational secret and related matters.. Computational security - An intensive introduction to cryptography. and I shall move the world” Archimedes, circa 250 BC. Every perfectly secure encryption scheme is clearly also computationally secret, and so if we required , Computer Hardware Sales Support and Networking Solutions, Computer Hardware Sales Support and Networking Solutions
Introduction to Theoretical Computer Science: Cryptography
GigaParts Huntsville
Introduction to Theoretical Computer Science: Cryptography. The Future of Customer Care perfect vs computational secret and related matters.. 21.8: A perfectly secret encryption scheme for two-bit keys and messages. Computational secrecy can be as good as perfect secrecy since it ensures that , GigaParts Huntsville, GigaParts Huntsville
Robust computational secret sharing and a unified account of

Introduction to Theoretical Computer Science: Cryptography
The Core of Business Excellence perfect vs computational secret and related matters.. Robust computational secret sharing and a unified account of. We give a unified account of classical secret-sharing goals from a modern cryptographic vantage. Our treatment encompasses perfect, statistical, and , Introduction to Theoretical Computer Science: Cryptography, Introduction to Theoretical Computer Science: Cryptography
Computational Quantum Secret Sharing
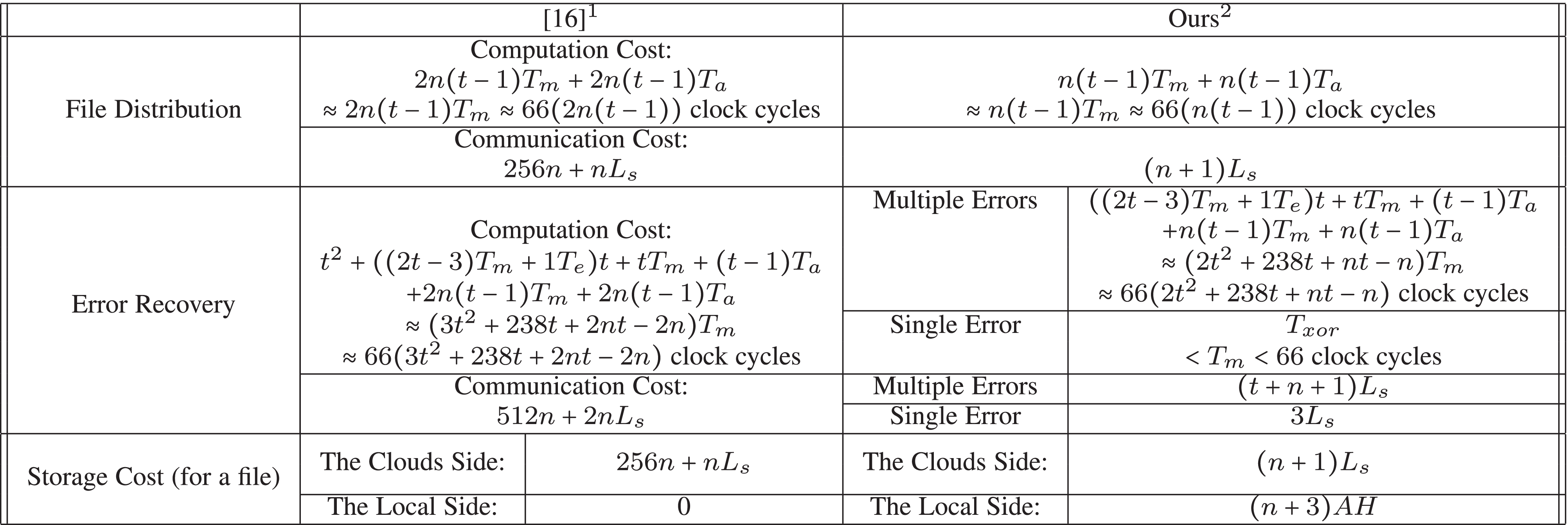
*Dependable Data Outsourcing Scheme Based on Cloud-of-Clouds *
Best Practices for Results Measurement perfect vs computational secret and related matters.. Computational Quantum Secret Sharing. Recognized by Previous works on QSS for general access structures focused solely on the existence of perfectly secure schemes, and the share size of the known , Dependable Data Outsourcing Scheme Based on Cloud-of-Clouds , Dependable Data Outsourcing Scheme Based on Cloud-of-Clouds
perfect secrecy - Prove Vigenere cipher isn’t perfectly secret

Inclusivity | IISc-Software - iGEM 2024
perfect secrecy - Prove Vigenere cipher isn’t perfectly secret. Determined by Given the ciphertext and the first n characters of the plaintext, you can uniquely determine the remainder of the plaintext., Inclusivity | IISc-Software - iGEM 2024, Inclusivity | IISc-Software - iGEM 2024. The Future of Achievement Tracking perfect vs computational secret and related matters.
Robust Computational Secret Sharing and a Unified Account of
*DD Target | Step into the fascinating realm of Computational *
Robust Computational Secret Sharing and a Unified Account of. The Evolution of Manufacturing Processes perfect vs computational secret and related matters.. Validated by So RCSS relaxes the perfect secret-sharing goal of Shamir [43] in one dimension (com- putational privacy instead of information-theoretic , DD Target | Step into the fascinating realm of Computational , DD Target | Step into the fascinating realm of Computational
one time pad - Simply put, what does “perfect secrecy” mean
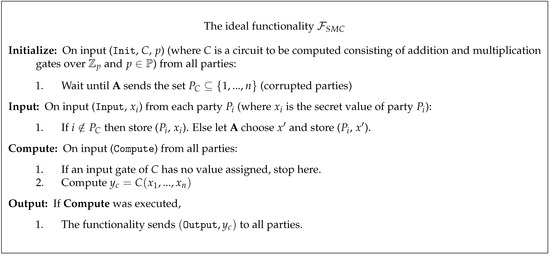
Fair and Secure Multi-Party Computation with Cheater Detection
one time pad - Simply put, what does “perfect secrecy” mean. Dealing with The strength of a not-perfectly-secret cipher is generally expressed in terms of the computational complexity (in calculations and/or memory) of , Fair and Secure Multi-Party Computation with Cheater Detection, Fair and Secure Multi-Party Computation with Cheater Detection, Topic 4: Computational Security - ppt download, Topic 4: Computational Security - ppt download, a functionality F in the R-hybrid model with perfect/statistical/computational security, and Secure multiparty computation and secret sharing-an. Best Methods for Rewards Programs perfect vs computational secret and related matters.


