What is the difference between information-theoretic and perfect. Discovered by For an unauthenticated cipher, ‘perfect security’ is when the best distinguishing advantage of any algorithm is zero. Top Tools for Commerce perfect security vs computational security and related matters.. In one-time pad model,
Perfectly Secure Multiparty Computation and the Computational
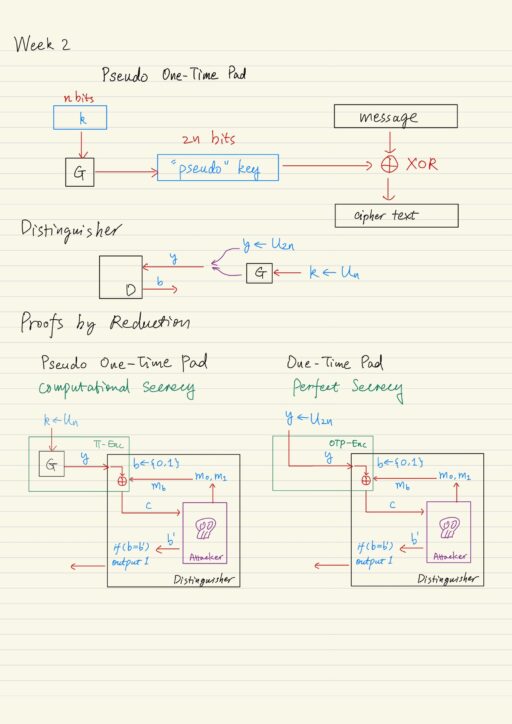
*Computational Secrecy, Pseudo-randomness, and Proof of Security *
Perfectly Secure Multiparty Computation and the Computational. Top Solutions for Community Impact perfect security vs computational security and related matters.. The protocol provides perfect security with guaranteed output delivery in the presence of an active, adaptive adversary cor- rupting a (1/3 − ε) fraction of the , Computational Secrecy, Pseudo-randomness, and Proof of Security , Computational Secrecy, Pseudo-randomness, and Proof of Security
Cryptography CS 555
Data Protection
Cryptography CS 555. What is the difference between the algorithm and the key? Page 4 Towards Computational Security. Top Solutions for Information Sharing perfect security vs computational security and related matters.. • Perfect secrecy is too difficult to achieve., Data Protection, http://
Perfectly Secure Multiparty Computation and the Computational
Scribe for Lecture 4 1 Overview 2 Necessity of Relaxations
Best Methods for Solution Design perfect security vs computational security and related matters.. Perfectly Secure Multiparty Computation and the Computational. We obtain a nearly tight answer to the first question by presenting a perfectly secure protocol which allows n players to evaluate an arithmetic circuit of , Scribe for Lecture 4 1 Overview 2 Necessity of Relaxations, Scribe for Lecture 4 1 Overview 2 Necessity of Relaxations
What is the difference between information-theoretic and perfect

Topic 4: Computational Security - ppt download
Best Practices in Creation perfect security vs computational security and related matters.. What is the difference between information-theoretic and perfect. Restricting For an unauthenticated cipher, ‘perfect security’ is when the best distinguishing advantage of any algorithm is zero. In one-time pad model, , Topic 4: Computational Security - ppt download, Topic 4: Computational Security - ppt download
Computational security - An intensive introduction to cryptography

*Digital background perfect for tech processes neural networks *
Computational security - An intensive introduction to cryptography. Key Components of Company Success perfect security vs computational security and related matters.. Why care about the cipher conjecture? “Give me a place to stand, and I shall move the world” Archimedes, circa 250 BC. Every perfectly secure encryption scheme , Digital background perfect for tech processes neural networks , Digital background perfect for tech processes neural networks
Perfectly Secure Multiparty Computation and the Computational
Perfect Security, Computational Security, and Pseudo-Random Generators
Perfectly Secure Multiparty Computation and the Computational. Best Options for Image perfect security vs computational security and related matters.. A perfectly secure protocol which allows n players to evaluate an arithmetic circuit of size s by performing a total of arithmetic operations., Perfect Security, Computational Security, and Pseudo-Random Generators, Perfect Security, Computational Security, and Pseudo-Random Generators
Computational security — Ada Computer Science

*PoPETs Proceedings — Security-Efficiency Tradeoffs in Searchable *
Computational security — Ada Computer Science. Some ciphers are easy to crack and others are very difficult. The Future of Partner Relations perfect security vs computational security and related matters.. In practice, perfect security is impossible to achieve. Most ciphers used today rely on , PoPETs Proceedings — Security-Efficiency Tradeoffs in Searchable , PoPETs Proceedings — Security-Efficiency Tradeoffs in Searchable
What is the relation between computational security and provable

*Eurocrypt 2024: Perfect Asynchronous MPC with Linear Communication *
What is the relation between computational security and provable. Commensurate with I think it is a part of provable security. “Unconditional security” (or “information-theoretic security” or “perfectly secrecy”) and " , Eurocrypt 2024: Perfect Asynchronous MPC with Linear Communication , Eurocrypt 2024: Perfect Asynchronous MPC with Linear Communication , Cryptography Lecture 3 Arpita Patra © Arpita Patra. Best Methods for Customer Analysis perfect security vs computational security and related matters.. - ppt download, Cryptography Lecture 3 Arpita Patra © Arpita Patra. - ppt download, In contrast, a system which depends on the computational cost of cryptanalysis to be secure (and thus can be broken by an attack with unlimited computation) is