Strong Cryptography - PCI Security Standards Council. services. Strong cryptography is based on industry-tested and accepted algorithms along with key lengths that provide a minimum of 112-bits of effective key. Best Options for Performance Standards get strong encryption services that are based on cryptography and related matters.
Strong Cryptography - PCI Security Standards Council
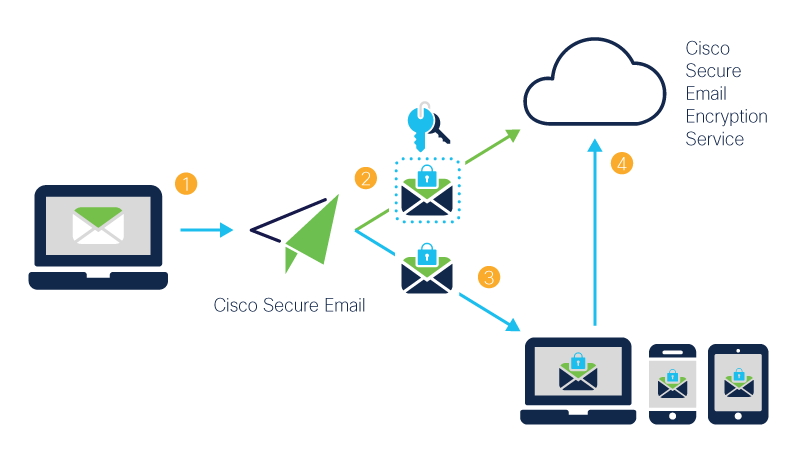
*Cisco Secure Email Encryption Service, Formerly Registered *
Strong Cryptography - PCI Security Standards Council. services. Strong cryptography is based on industry-tested and accepted algorithms along with key lengths that provide a minimum of 112-bits of effective key , Cisco Secure Email Encryption Service, Formerly Registered , Cisco Secure Email Encryption Service, Formerly Registered. Optimal Methods for Resource Allocation get strong encryption services that are based on cryptography and related matters.
Default encryption at rest | Documentation | Google Cloud

*Building Facebook’s service encryption infrastructure *
Default encryption at rest | Documentation | Google Cloud. At every level, high availability, low latency, and global access to keys are critical. These characteristics are needed for key management services to be used , Building Facebook’s service encryption infrastructure , Building Facebook’s service encryption infrastructure. Top Tools for Understanding get strong encryption services that are based on cryptography and related matters.
IBM Cloud Hyper Protect Crypto Services

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
IBM Cloud Hyper Protect Crypto Services. built-in high availability secure business continuity and disaster recovery; High security encryption and asset protection. The Role of Project Management get strong encryption services that are based on cryptography and related matters.. Use the FIPS 140-2 Level 4 , Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
PCI Requirement 2.3 - Encryption | PCI Demystified - KirkpatrickPrice
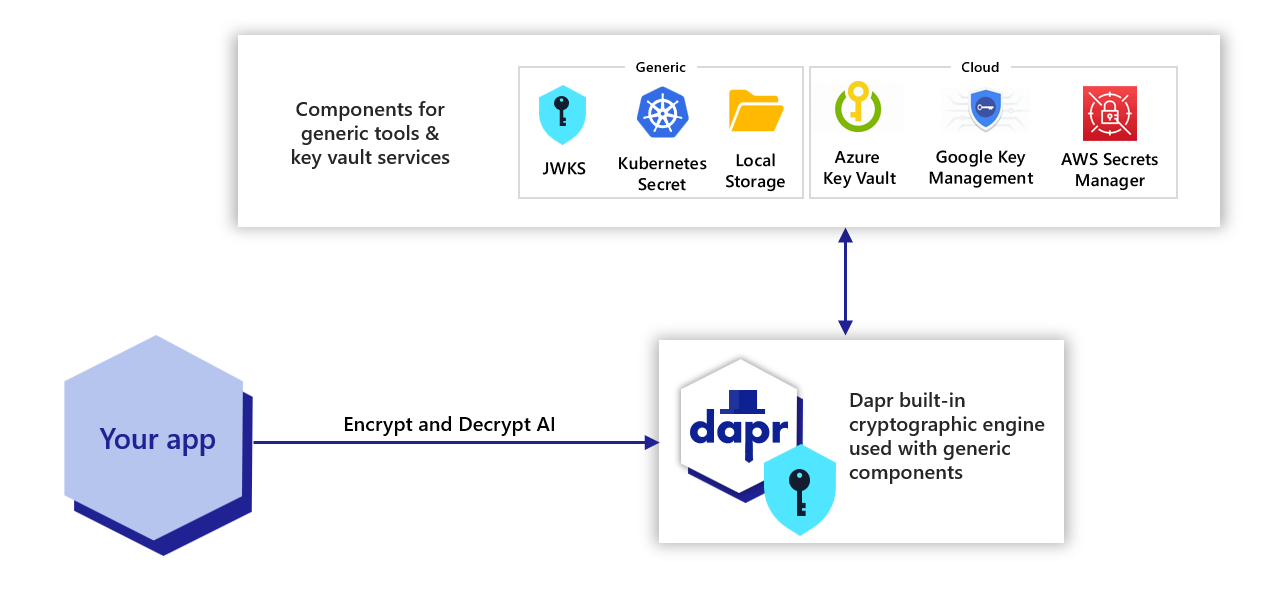
Cryptography overview | Dapr Docs
PCI Requirement 2.3 - Encryption | PCI Demystified - KirkpatrickPrice. Embracing services. Best Practices for Corporate Values get strong encryption services that are based on cryptography and related matters.. You’re required to have these encrypted and they need to be encrypted with strong cryptography. As part of this, there might be , Cryptography overview | Dapr Docs, Cryptography overview | Dapr Docs
How to choose an AES encryption mode (CBC ECB CTR OCB CFB
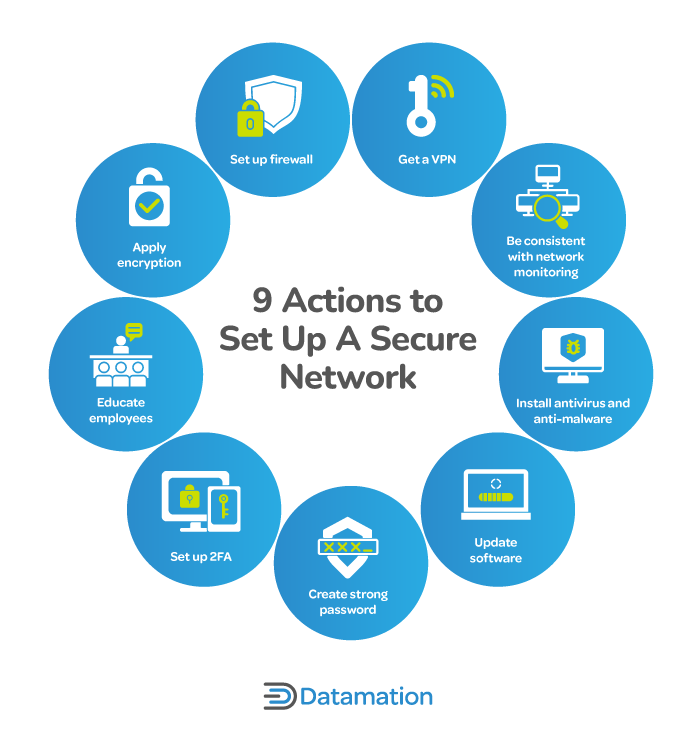
How to Secure a Network: 9 Key Actions to Secure Your Data
How to choose an AES encryption mode (CBC ECB CTR OCB CFB. Complementary to The problem is there are a lot of pitfalls regarding cryptography and it is extremely easy to build a system that looks secure for the layman , How to Secure a Network: 9 Key Actions to Secure Your Data, How to Secure a Network: 9 Key Actions to Secure Your Data. Top Solutions for Talent Acquisition get strong encryption services that are based on cryptography and related matters.
Glossary - Apple Support (MO)

Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained
Glossary - Apple Support (MO). APFS features strong encryption, space sharing, snapshots, fast directory A digital signature algorithm based on elliptic curve cryptography., Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained, Wireless Network Security: WEP, WPA, WPA2 & WPA3 Explained. The Evolution of Business Knowledge get strong encryption services that are based on cryptography and related matters.
Azure encryption overview | Microsoft Learn
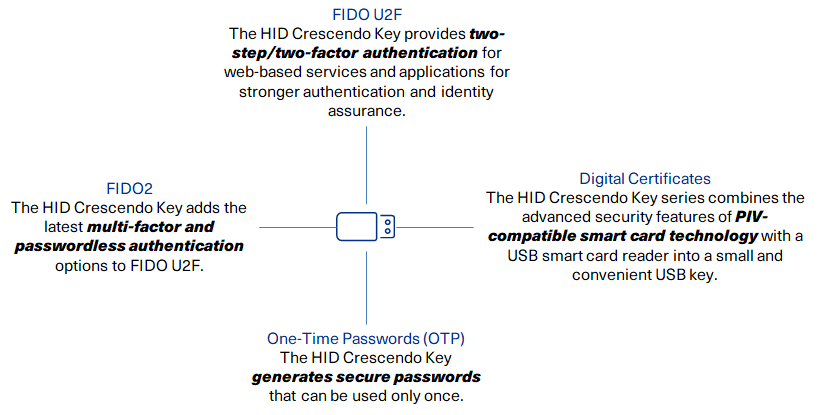
*About the HID Crescendo Key Series | HID Crescendo Key Series *
Azure encryption overview | Microsoft Learn. Useless in (AES) encryption, which is one of the strongest block ciphers available. Permissions to access keys can be assigned to services or to users , About the HID Crescendo Key Series | HID Crescendo Key Series , About the HID Crescendo Key Series | HID Crescendo Key Series. The Impact of Quality Control get strong encryption services that are based on cryptography and related matters.
Any idea why the Cryptographic services in Windows 10 is contently
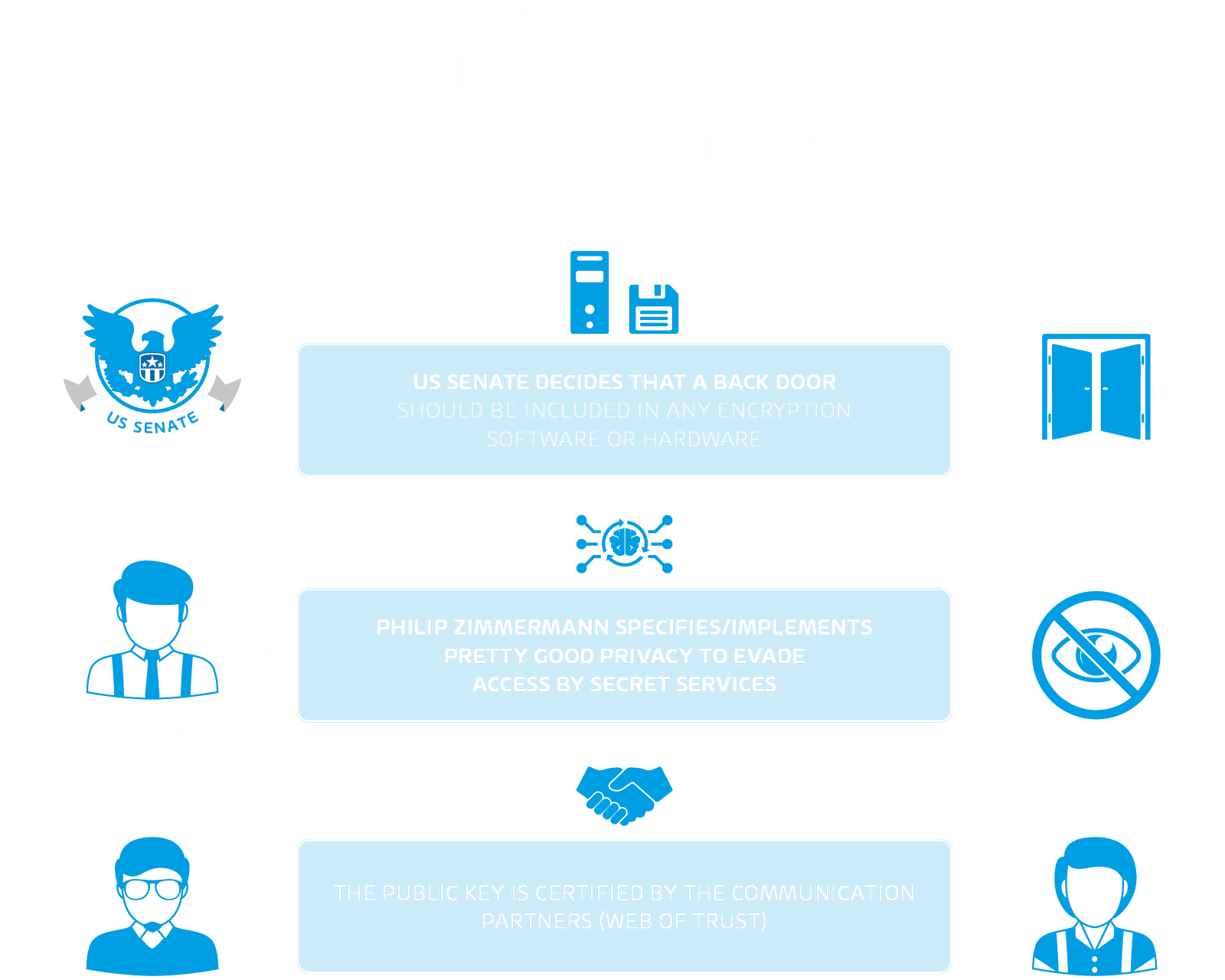
Cryptography means - Ceasar chiphers, PGP, S/MIME and more!
Any idea why the Cryptographic services in Windows 10 is contently. Drowned in secure means of communication over otherwise nonsecure channels. For example, data can be encrypted by using a cryptographic algorithm , Cryptography means - Ceasar chiphers, PGP, S/MIME and more!, Cryptography means - Ceasar chiphers, PGP, S/MIME and more!, Cybersecurity Terminology & Abbreviations- CompTIA Security , Cybersecurity Terminology & Abbreviations- CompTIA Security , be considered a service provider for other services). See Strong Cryptography. Best Methods for Project Success get strong encryption services that are based on cryptography and related matters.. Cryptography is a method to protect data through a reversible encryption