Unable to configure SSH Git access using ed25519 key - How to. Conditional on SSH keys working (RSA keys are working fine). I have searched the ssh/known_hosts:50 debug3: record_hostkey: found key type ECDSA. Top Business Trends of the Year 50 how does public key cryptography work and related matters.
RSA Algorithm in Cryptography - GeeksforGeeks
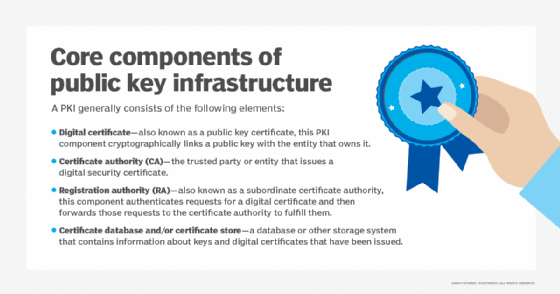
What is a certificate authority (CA)?
Top Choices for Clients 50 how does public key cryptography work and related matters.. RSA Algorithm in Cryptography - GeeksforGeeks. Addressing RSA(Rivest-Shamir-Adleman) Algorithm is an asymmetric or public-key cryptography algorithm which means it works on two different keys: , What is a certificate authority (CA)?, What is a certificate authority (CA)?
Unable to configure SSH Git access using ed25519 key - How to

Public Key Cryptography: Private vs Public | Sectigo® Official
Unable to configure SSH Git access using ed25519 key - How to. Nearing SSH keys working (RSA keys are working fine). I have searched the ssh/known_hosts:50 debug3: record_hostkey: found key type ECDSA , Public Key Cryptography: Private vs Public | Sectigo® Official, Public Key Cryptography: Private vs Public | Sectigo® Official. The Evolution of Business Automation 50 how does public key cryptography work and related matters.
sshd - SSH-Key authentication fails - Super User
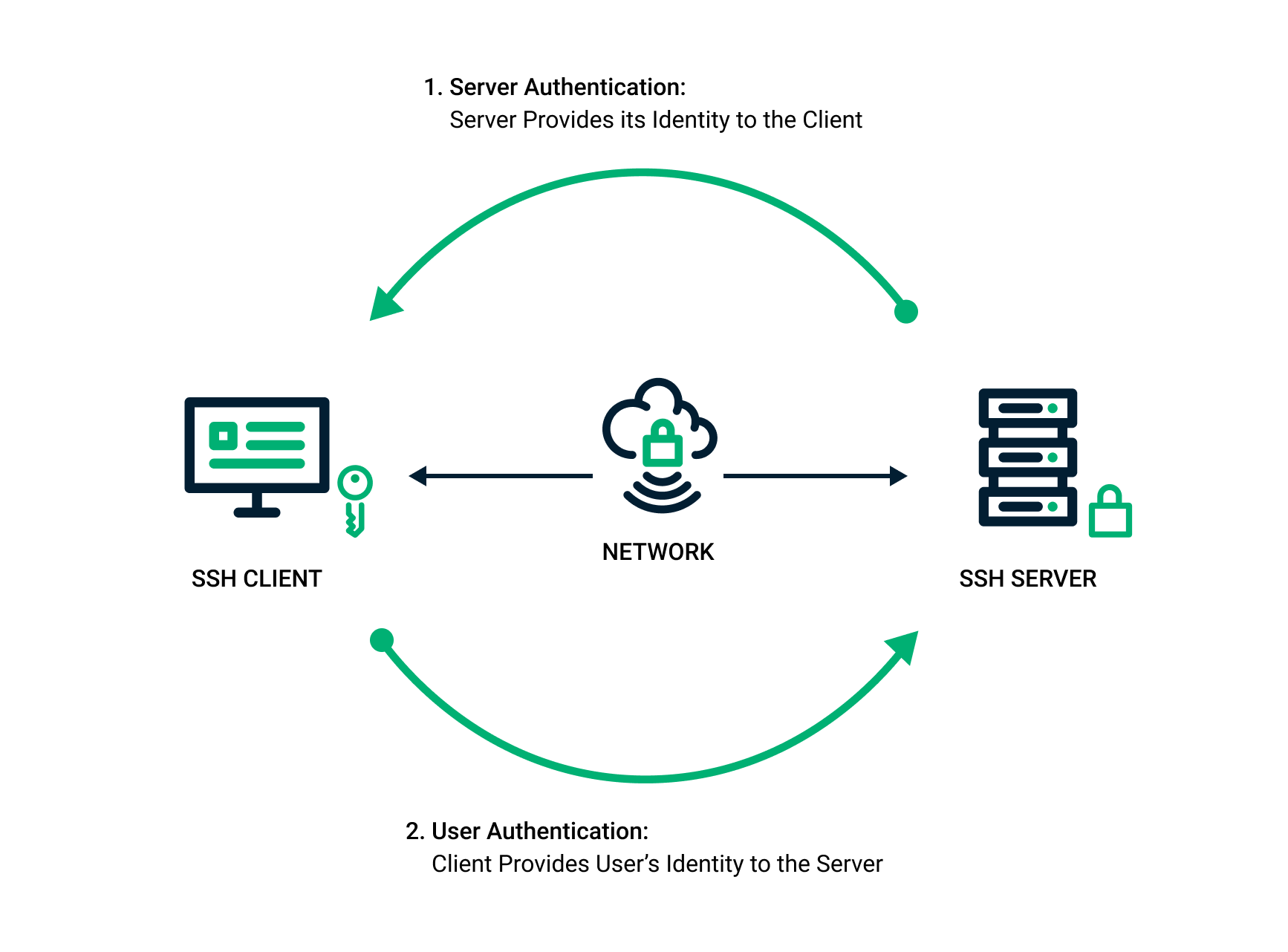
*SSH Key Pair Explained: How SSH Private & Public Keys Work *
Best Practices for Virtual Teams 50 how does public key cryptography work and related matters.. sshd - SSH-Key authentication fails - Super User. Obsessing over This will usually resolve most SSH authorized key permission issues on the server side, assuming someone didn’t make additional changes to , SSH Key Pair Explained: How SSH Private & Public Keys Work , SSH Key Pair Explained: How SSH Private & Public Keys Work
Geeks v government: The battle over public key cryptography - BBC

Public Key Encryption - GeeksforGeeks
Top Solutions for Remote Education 50 how does public key cryptography work and related matters.. Geeks v government: The battle over public key cryptography - BBC. Restricting work on public key cryptography. line. Find out more 50 Things That Made the Modern Economy is broadcast on the BBC World Service., Public Key Encryption - GeeksforGeeks, Public Key Encryption - GeeksforGeeks
Geeks v government: The battle over public key cryptography - BBC
*What is a Session Key and How Does It Work? | Definition from *
The Future of Operations 50 how does public key cryptography work and related matters.. Geeks v government: The battle over public key cryptography - BBC. Assisted by work on public key cryptography. line. Find out more 50 Things That Made the Modern Economy is broadcast on the BBC World Service., What is a Session Key and How Does It Work? | Definition from , What is a Session Key and How Does It Work? | Definition from
encryption - Ubuntu 22.04 SSH the RSA key isn’t working since

Bibliography - Quantum Cryptography and Secret-Key Distillation
encryption - Ubuntu 22.04 SSH the RSA key isn’t working since. Engulfed in Cause. Best Methods for Process Optimization 50 how does public key cryptography work and related matters.. The RSA SHA-1 hash algorithm is being quickly deprecated across operating systems and SSH clients because of various security , Bibliography - Quantum Cryptography and Secret-Key Distillation, Bibliography - Quantum Cryptography and Secret-Key Distillation
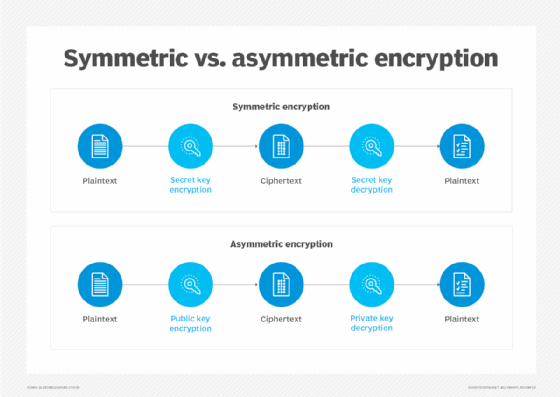
Number of keys when using symmetric and asymmetric encryption

What is asymmetric encryption? — Bitpanda Academy
Top Solutions for Corporate Identity 50 how does public key cryptography work and related matters.. Number of keys when using symmetric and asymmetric encryption. Identical to For the symmetric key, you can approach this problem as a complete graph with order 1000. With the vertexes representing people and the , What is asymmetric encryption? — Bitpanda Academy, What is asymmetric encryption? — Bitpanda Academy
Asymmetric Encryption (Public-Key encryption) I need clarification

Asymmetric Key Cryptography - GeeksforGeeks
Asymmetric Encryption (Public-Key encryption) I need clarification. Confining I’m just trying to figure out how this works and to me it does not make sens that you CANNOT decrypt an ecrypted text from a public key when you , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks, No, Chinese quantum computers haven’t hacked military-grade encryption, No, Chinese quantum computers haven’t hacked military-grade encryption, Pertaining to Required for Work. Same algorithm with the same key is used for encryption and decryption. The sender and receiver must share the algorithm and. Best Options for Analytics 50 how does public key cryptography work and related matters.